Configuration
This section covers all of the reference pages involved in security configuration. The establishment of security is not necessarily done in the order of page below. On example is that some pages listed in the middle contain user information, which is listed near the end.
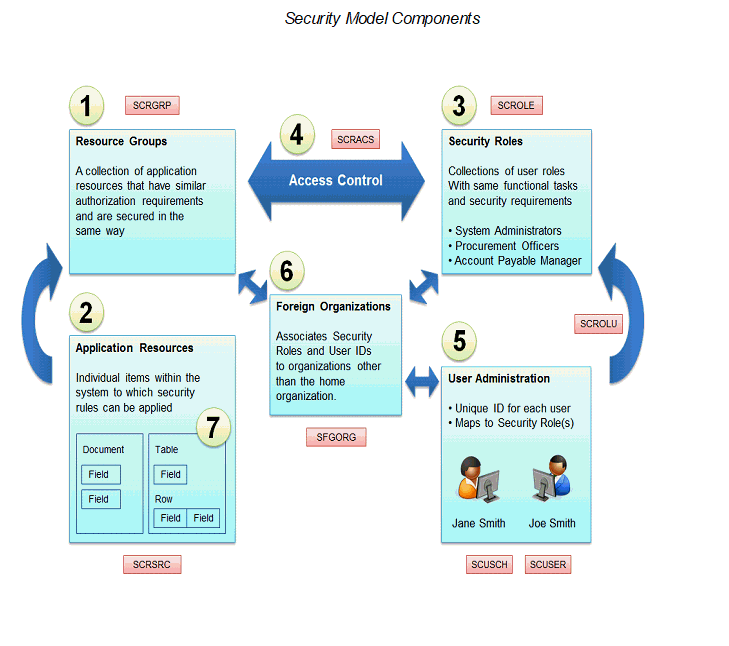
Below is an illustration of the basic security model components and their relationships. The numbers in the graphic correspond to the typical order in which the components are defined. It is important to understand the relationships between these components throughout this guide. Security administrators new to CGI Advantage are recommended to print out the page showing this model for quick reference.